WordPress is the most popular CMS and is being used by many popular publications. Millions of WordPress websites are at risk after this unpatched logical vulnerability was found in the WordPress.
This logical vulnerability allows hackers to reset the admin password of a WordPress website. It was discovered by Polish security researcher Dawid Golunski of Legal Hackers who reported this flaw to WordPress security team last year in July. But the flaw was ignored leaving millions of WordPress based websites vulnerable.
Dawid Golunski has found critical vulnerabilities in several popular and widely used products including SquirrelMai, Swiftmailer, PHPMailer, MySQL, vBulletin, CakePHP and more.
He reported the flaw directly by using security contact email and via HackerOne website, but never nothing was done. So, he decided to wrote in a public advisory.
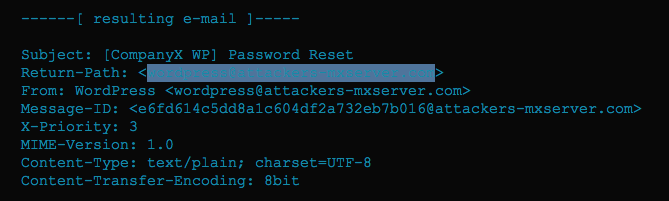
This zero-day flaw is related to how WordPress sites put together the password reset emails. It alters “From” and “Return-Path” parameters. The worst part is that it affects all WordPress version.
This allows an attacker to craft a malicious HTTP request and trigger a tainted password reset operation by injecting a custom SERVER_NAME variable.
It looks like the attacker will only be able to send a password reset email to legitimate site owner with wrong Sender address, but this can be quite dangerous. Golunski details how it can be done. The attacker can flood the site owner’s email inbox with junk emails. When the legitimate user’s inbox is full, the email server will return the email back to its sender. In this case, it is the “Return-Path” value, the attacker’s email.
If the victim is on leave and is using auto responder that attach the copy of the email sent in the body of the auto-replied message, the attacker can easily get a password reset link.
These methods to exploit the flaw are complicated. This could be a reason why WordPress security team didn’t give it a priority. Few other security researchers also have the same view. They said that the vulnerability is not as critical as advertised.
I also think that the attack will not be easy to exploit but sophisticated hackers can still manage to exploit this flaw successfully. So, ignoring it can be a big risk when the vulnerability is available in public domain.
Since the vulnerability is now publicly available with no patch available, WordPress admins are at the risk. Hackers will surely try to exploit it in several ways. If you own a WordPress based website and wants to be safe, you can update server configuration to enable UseCanonicalName to enforce static/predefined SERVER_NAME value.