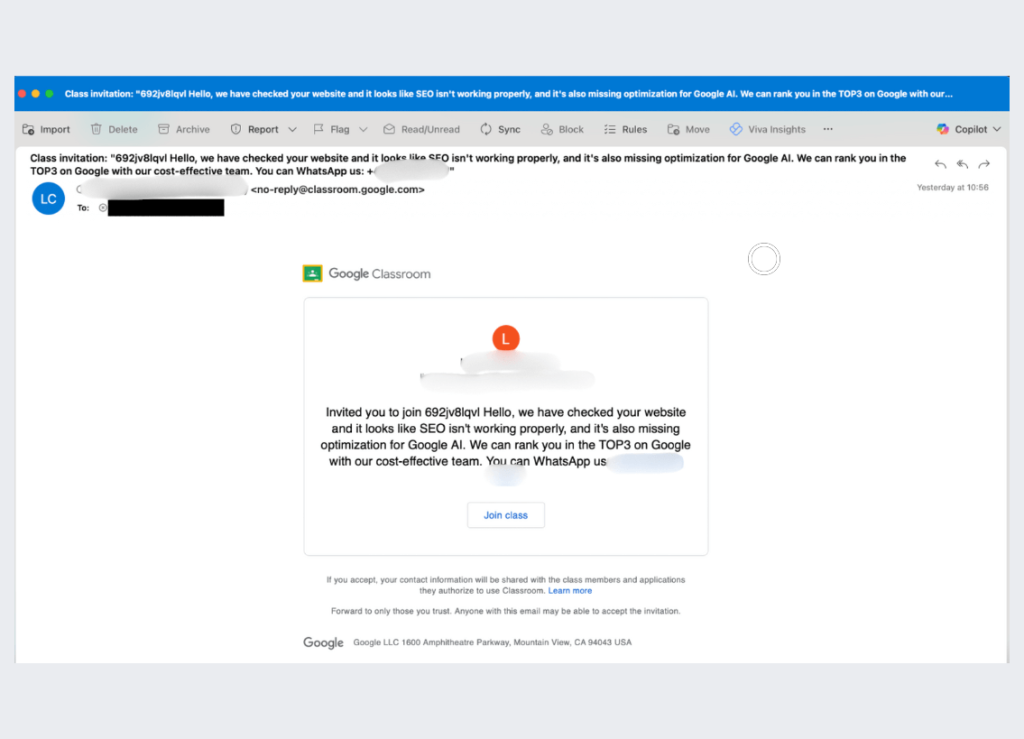
A new phishing campaign has been discovered where hackers are abusing Google Classroom to target students, educators, and even companies across different industries.
Researchers at Check Point reported that attackers sent out over 115,000 phishing emails in five separate attack waves, reaching nearly 13,500 organizations worldwide. These emails were disguised as Google Classroom invitations and promote fake “commercial offers” like SEO services or product pitches.
Because the attack is hosted on Google’s own infrastructure, it often slips past traditional email security tools. Security systems usually trust links from well-known platforms. This makes these phishing attempts even more dangerous.
Check Point explains that this campaign shows how attackers are increasingly weaponizing legitimate cloud services to hide malicious activity. Google Classroom is widely used in schools and universities, and piggybacking on it allows criminals to easily trick users into clicking fake invitations.
The biggest issue here is not just the scale of the attack but how it bypasses normal defenses. Traditional email filters cannot block these phishing attempts since the links look like genuine Google services. That makes the human factor the weakest link. One wrong click can expose personal data, login credentials, or even corporate accounts.
Hackers are not just targeting schools. The campaign also went after businesses across multiple sectors. This shows how education platforms are now being misused for large-scale cybercrime beyond their original audience.
Check Point recommends organizations take phishing awareness training more seriously. Employees and students should learn to verify invitations before clicking and be suspicious of unexpected requests. The research also highlights the need for AI-powered detection systems that go beyond traditional email gateways.
Earlier this year, similar phishing techniques were seen targeting Microsoft services through fake login pages. Cybercriminals even used malvertising campaigns that spread malware without relying on email, again bypassing common filters.
Hackers know that people trust platforms like Google Classroom. That trust is now being exploited to run sophisticated social engineering campaigns. The lesson is clear: even if a message looks like it comes from a trusted service, do not click blindly. Always verify before responding—because once attackers get access, the damage can spread quickly across entire organizations.