Cloudflare has released its Q2 2025 DDoS Threat Report, and it shows a major rise in hyper-volumetric DDoS attacks. While the total number of DDoS attacks dropped in Q1 2025, the scale and power of attacks went up.
Cloudflare says it automatically blocked a record-breaking 7.3 terabits per second (Tbps) attack this quarter. It was the largest ever recorded to date. These hyper-volumetric attacks, which include L3/L4 floods over 1 Tbps or 1 billion packets per second, are now happening at an average of 71 times a day.
In Q2 2025, Cloudflare mitigated 7.3 million DDoS attacks. While that is significantly lower than the 20.5 million attacks seen in Q1, driven by a massive 18-day offensive earlier this year. Compared to the same quarter last year, the volume of attacks is up by 44%.
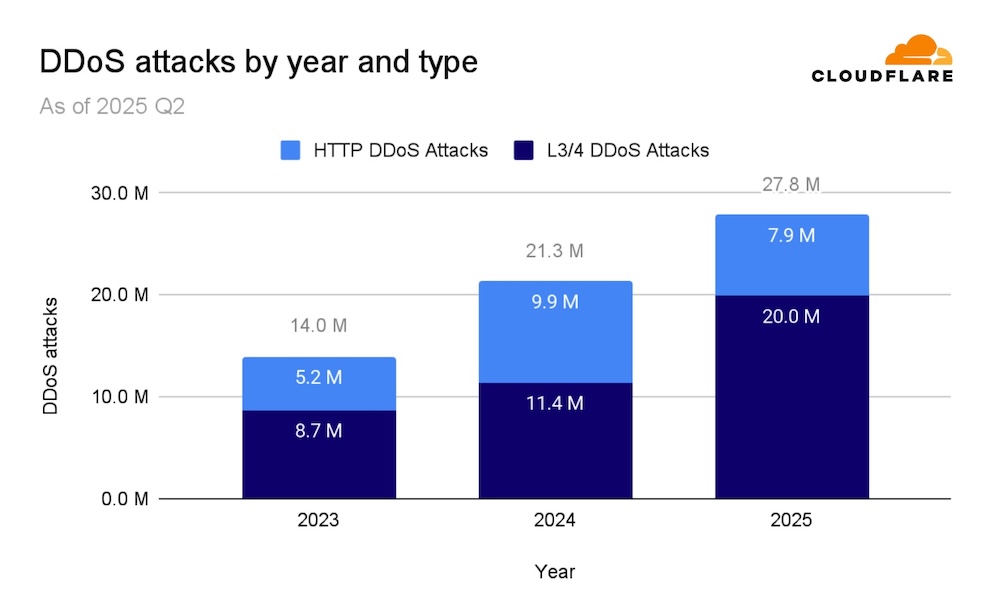
Cloudflare says attacks exceeding 100 million packets per second rose by 592% quarter-over-quarter. Those crossing the 1 Tbps mark or 1 billion packets per second doubled. HTTP-based DDoS attacks, which target websites and APIs, were up 9% from Q1 and have grown by 129% compared to Q2 2024.
June 2025 accounted for nearly 38% of all attacks seen during the quarter. One high-profile target was an independent news outlet in Eastern Europe, which reportedly came under attack after publishing content related to LGBTQ Pride Month.
Most DDoS attacks are short. Even the record 7.3 Tbps attack lasted only 45 seconds. Attackers use short, high-volume bursts to avoid detection and cause fast disruption. This makes it harder to stop the attack if there is no real-time protection in place. Cloudflare’s automatic systems detect and block such attacks in real-time.
The report also highlights that 71% didn’t even know who attacked them. 63% of those who claimed to know blamed competitors, and 21% blamed state-sponsored actors.
Ransom DDoS (RDDoS) attacks also increased. It was 68% up from last quarter and 6% from Q2 2024. A third of victims in June received ransom threats.
If I talk about the most attacked countries, China tops the list, and India ranks in the 4th place. The United States is not even in the top 10.
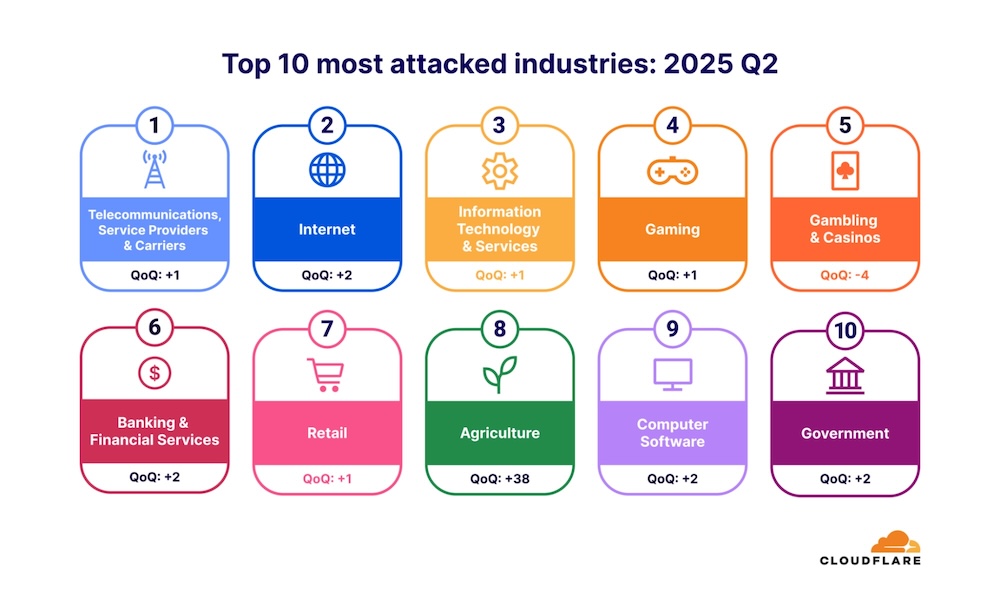
Telecom and ISPs, Internet sector, IT & Services, Gaming, Gambling, and Banking were the most attacked industries in descending order. Interestingly, the agriculture industry saw a massive jump. It moves up 38 spots to enter the top 10 list of targeted sectors.
Cloudflare also revealed the top sources of attacks; however, the reported location is of botnet nodes or VPN endpoints. Indonesia, Singapore, and Hong Kong were the top sources of these DDOS attacks.
DNS floods remained the most common L3/L4 DDoS method and accounted for nearly a third of attacks. These are followed by SYN floods and UDP floods. Meanwhile, Cloudflare’s systems detected a growing number of HTTP floods driven by known botnets. The report also highlights a rise in legacy and lesser-known attack types.
Most attacks may be short and under 500 Mbps, but Cloudflare warns that even these can disrupt unprotected systems. A typical web server, depending on its setup, can handle only up to 940 Mbps or 100,000 packets per second. So, a “small” attack could easily knock services offline if defenses are not in place.