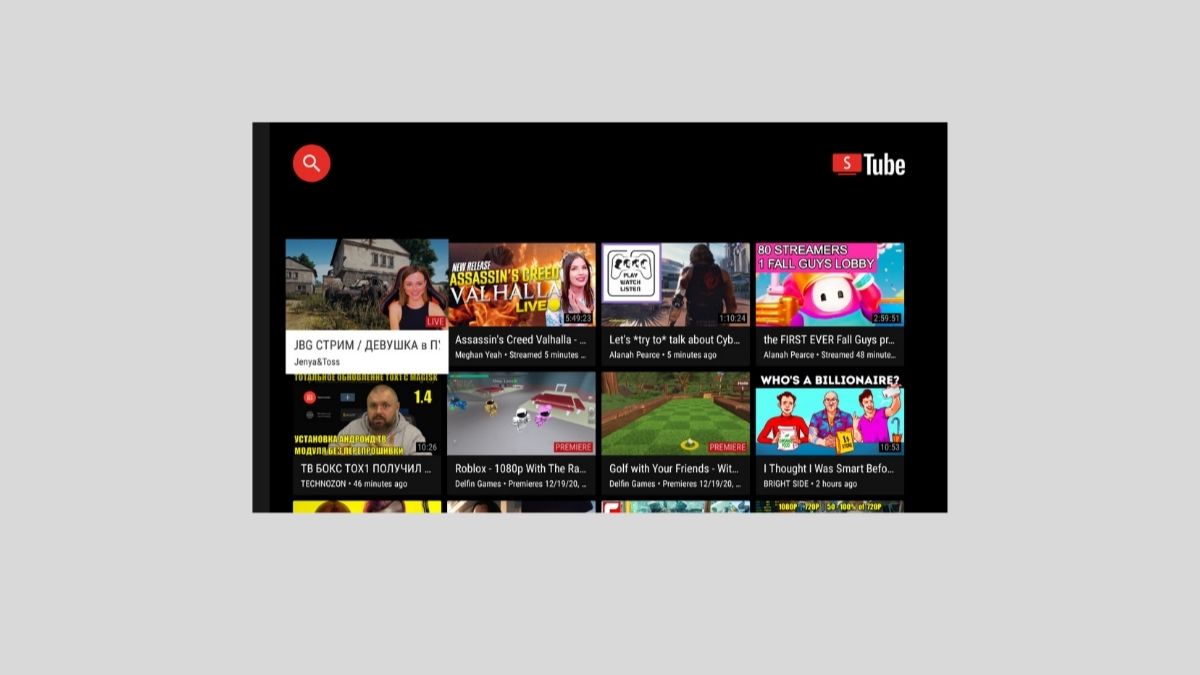
The popular SmartTube YouTube client for Android TV has been compromised. An attacker gained access to the developer’s signing keys and pushed a malicious update to users.
The breach came to light when several users reported that Play Protect, Android’s built-in antivirus, flagged SmartTube as risky. The developer, Yuriy Yuliskov, confirmed that his keys were stolen last week, which allowed malware to be injected into the app.
SmartTube is a third-party YouTube client designed for Android TVs, Fire TV sticks, Android TV boxes, and similar devices. Unlike the official YouTube app, SmartTube is free, blocks ads, and works smoothly even on devices with low processing power. It supports features like video search, playlists, and personalized recommendations.
The compromised version, 30.51, included a hidden library called libalphasdk.so. This file does not exist in the public code and was silently added to release builds. According to Yuliskov, this library runs in the background, fingerprints the device, connects to a remote server, and sends or receives data without any visible signs.
While there is no evidence that user accounts were stolen or devices were used in botnets, the potential risk remains high. Yuliskov has revoked the old signature and plans to release a new version with a new app ID. Users are advised to switch to the safe version once available.
Until then, users should stay on known safe builds, avoid logging in with premium accounts, and turn off auto-updates. Impacted users should also reset their Google Account passwords and check for unauthorized access.
According to the developer, the compromised versions appear to be 30.43 to 30.47. Builds from 30.55 onward use a new key and are considered secure. Yuliskov says he cleaned his development environment and removed malware after discovering the breach.
The community is waiting for a detailed post-mortem from the developer. Meanwhile, caution is strongly advised for anyone using SmartTube on Android TV.