Security researchers at Zscaler ThreatLabz have uncovered a new wave of Anatsa malware (TeaBot) campaigns on the Google Play Store. The latest variant is more advanced, expanding its reach to over 831 financial institutions worldwide, including banks and cryptocurrency platforms.
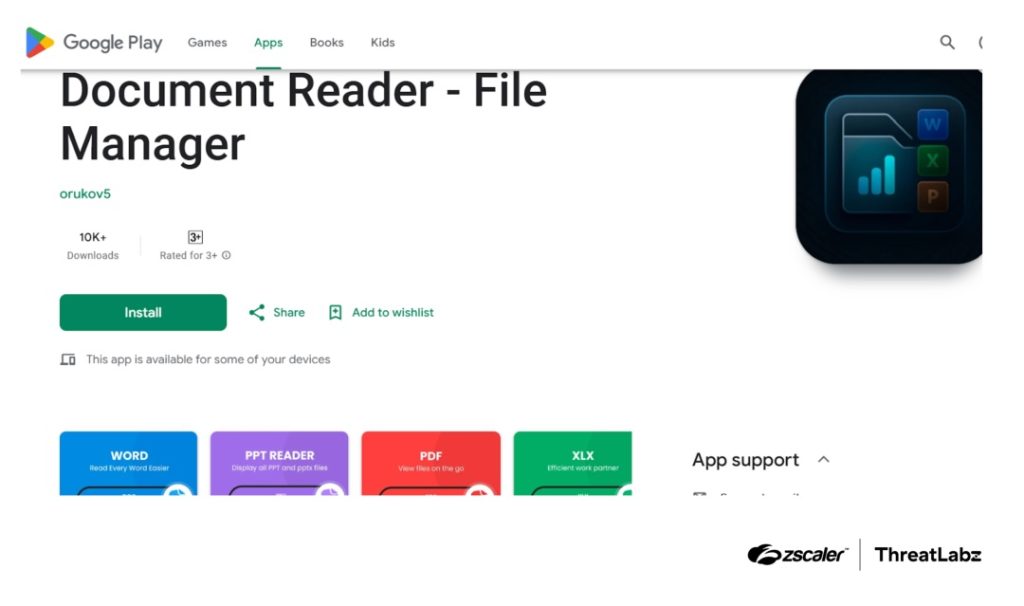
Attackers are using document reader apps on the Play Store as droppers. These apps appear harmless but secretly download the Anatsa payload from remote servers once installed. Some of these apps surpassed 50,000 downloads before being reported and removed.
Technical Advancements
The latest Anatsa campaign introduces new anti-analysis techniques.
- Strings are decrypted at runtime using a dynamic DES key, making static analysis difficult.
- The malware performs device checks and emulation detection to avoid sandbox testing.
- If the device is unsuitable, the app displays a file manager view to look legitimate.
Unlike earlier versions that relied on remote DEX loading, the malware now directly installs its payload for improved reliability. It also frequently alters its package names and installation hashes to bypass detection.
Once installed, Anatsa requests accessibility permissions. If granted, it automatically enables other permissions such as READ_SMS, RECEIVE_SMS, and SYSTEM_ALERT_WINDOW.
The malware connects to its command-and-control servers using simple XOR encryption. It can then push fake banking login screens that mimic real apps to trick users into entering their credentials. These stolen details are sent back to attackers.
Alongside Anatsa, Zscaler researchers flagged 77 other malicious apps across different malware families, collectively reaching over 19 million installs. Banking trojans like Anatsa and adware apps are on the rise, while older threats such as Facestealer and Coper have declined.
The report highlights the ongoing risk of malware slipping past Google Play protections. Users are advised to verify app permissions, avoid unknown developers, and update their devices with the latest security patches.